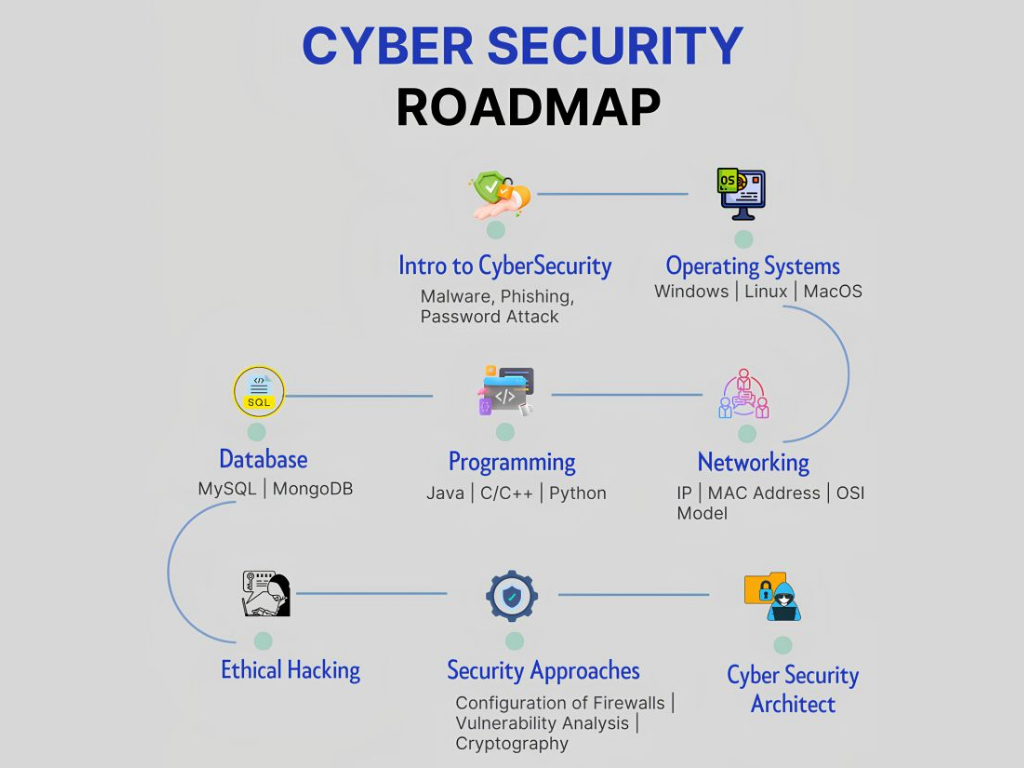
What is Cyber Security?
Cyber Security is the practice of protecting systems, networks, and data from digital attacks, unauthorized access, or damage. It encompasses a range of processes, technologies, and practices designed to secure computers, networks, and data from malicious attacks, damage, or unauthorized access. In today’s digital world, where almost everything is interconnected, cyber security is vital for protecting sensitive information, maintaining the integrity of systems, and ensuring the availability of critical services. Cyber security involves multiple layers of defense, spread across the computers, networks, programs, or data that one intends to keep safe. There are various types of cyber threats, including hacking, malware, phishing, ransomware, and social engineering, each requiring specific countermeasures.
Types of Cyber Security Engineers and Their Roadmaps
Cyber security engineers specialize in different areas depending on their roles and the needs of their
organizations. Below are some of the main types of cyber security engineers, their roles, and the roadmaps to
becoming one:
1. Network Security Engineer:
* Role: Focuses on protecting an organization’s network infrastructure from unauthorized access, misuse, or
attack.
This includes configuring firewalls, monitoring network traffic, and implementing VPNs and IDS/IPS systems.
* Skills Required:
* Networking basics (TCP/IP, DNS, HTTP/S)
* Firewalls, VPNs, IDS/IPS systems
* Network protocols and architecture
* Vulnerability assessment and threat management
* Roadmap:
* Step 1: Learn networking fundamentals, including TCP/IP, subnetting, and routing protocols.
* Step 2: Gain knowledge of basic security principles and the OSI model.
* Step 3: Learn about firewalls, VPNs, and IDS/IPS technologies.
* Step 4: Get hands-on experience with network security tools (e.g., Wireshark, Nmap).
* Step 5: Earn certifications like CompTIA Network+, CompTIA Security+, and Cisco CCNA Security.
* Step 6: Gain experience in network architecture and advanced security practices like penetration testing.
2. Application Security Engineer:
* Role: Ensures the security of software applications by identifying and mitigating vulnerabilities in code.
They work closely with development teams to integrate security practices into the software development lifecycle
(SDLC).
* Skills Required:
* Secure coding practices (e.g., OWASP Top 10)
* Application security testing (SAST, DAST)
* Software development and scripting languages (e.g., Python, Java)
* Encryption and authentication methods
* Roadmap:
* Step 1: Learn one or more programming languages such as Python, Java, or C#.
* Step 2: Study secure coding practices, including how to avoid common vulnerabilities like SQL injection
and
XSS.
* Step 3: Learn about application security testing tools like Burp Suite, Veracode, and Checkmarx.
* Step 4: Gain knowledge of the software development lifecycle (SDLC) and DevSecOps.
* Step 5: Obtain certifications like Certified Secure Software Lifecycle Professional (CSSLP) or Certified
Ethical Hacker (CEH).
* Step 6: Gain hands-on experience by performing code reviews, penetration testing, and vulnerability
assessments.
3. Cloud Security Engineer:
* Role: Focuses on securing cloud environments, including designing secure cloud architectures, managing
cloud
security configurations, and ensuring compliance with cloud security standards.
* Skills Required:
* Cloud platforms (AWS, Azure, GCP)
* Identity and Access Management (IAM)
* Cloud security best practices
* Compliance and governance in cloud environments
* Roadmap:
* Step 1: Learn the basics of cloud computing and cloud service providers like AWS, Azure, or Google Cloud.
* Step 2: Study cloud security fundamentals, including encryption, IAM, and secure cloud architecture.
* Step 3: Gain hands-on experience with cloud security tools and services like AWS Shield, Azure Security
Center, or GCP Security.
* Step 4: Obtain certifications like AWS Certified Security – Specialty or Certified Cloud Security
Professional
(CCSP).
* Step 5: Explore advanced topics like container security, serverless security, and multi-cloud security
strategies.
4. Incident Response Engineer:
* Role: Specializes in responding to and managing cyber security incidents. This involves identifying the
scope
of an attack, containing it, eradicating the threat, and recovering systems. They also analyze incidents to
prevent future occurrences.
* Skills Required:
* Threat detection and analysis
* Incident handling and forensics
* Malware analysis
* Communication and reporting
* Roadmap:
* Step 1: Learn the basics of incident response, including the incident response lifecycle.
* Step 2: Study digital forensics, focusing on the collection and analysis of digital evidence.
* Step 3: Gain expertise in malware analysis and reverse engineering.
* Step 4: Obtain certifications like Certified Incident Handler (GCIH) or Certified Computer Forensics
Examiner
(CCFE).
* Step 5: Practice by participating in incident response simulations and real-world scenarios.
5. Penetration Tester (Ethical Hacker):
* Role: Performs simulated cyber attacks to find vulnerabilities in systems, networks, and applications. The
goal is to identify weaknesses before malicious actors can exploit them.
* Skills Required:
* Penetration testing methodologies (e.g., OWASP, PTES)
* Exploitation techniques and tools (e.g., Metasploit, Burp Suite)
* Social engineering
* Vulnerability assessment and reporting
* Roadmap:
* Step 1: Learn the basics of ethical hacking, including the phases of penetration testing.
* Step 2: Gain hands-on experience with penetration testing tools like Metasploit, Nmap, and Burp Suite.
* Step 3: Study web application and network penetration testing techniques.
* Step 4: Obtain certifications like Offensive Security Certified Professional (OSCP) or Certified Ethical
Hacker (CEH).
* Step 5: Participate in bug bounty programs and CTF (Capture the Flag) competitions to sharpen your skills.
Why Cyber Security?
1. High Demand: The frequency and sophistication of cyber attacks are increasing, leading to a growing demand for skilled cyber security professionals across all industries
2. Job Security: Cyber security is a critical field, and the need for experts is expected to grow continuously, providing long-term job security.
3. Impactful Work: Cyber security professionals protect vital systems and sensitive information, playing a crucial role in safeguarding businesses, governments, and individuals.
4. Continuous Learning: The field of cyber security is dynamic, with new threats and technologies emerging regularly. This ensures that the work remains challenging and offers opportunities for continuous learning and professional growth.
5. Lucrative Salaries: Due to the high demand for skilled professionals, cyber security roles often come with competitive salaries and benefits.

How to Learn Cyber Security
...
...
1. Choose Your Path:
* Decide on a specialization (e.g., network security, application security, cloud security, incident
response,
or penetration testing) or start with a generalist approach to cyber security.
2. Start with the Basics:
* Networking: Understand how data flows across networks, including knowledge of TCP/IP, DNS, HTTP/S, and
network
devices.
* Operating Systems: Gain a strong understanding of Linux and Windows operating systems, as they are
commonly
used in cyber security.
* Security Fundamentals: Study basic concepts like encryption, firewalls, access control, and the CIA triad
(Confidentiality, Integrity, Availability).
3. Gain Hands-On Experience:
* Set Up a Home Lab: Create a virtual lab environment using tools like VirtualBox or VMware to practice
different security tasks.
* Capture the Flag (CTF) Challenges: Participate in CTF challenges on platforms like Hack The Box,
TryHackMe, or
CTFtime to build your skills in a practical, competitive setting.
* Online Labs: Use platforms like Cybrary, RangeForce, or PentesterLab for guided hands-on learning.
4. Learn Tools and Techniques:
* Security Tools: Get familiar with tools like Wireshark, Nmap, Metasploit, Nessus, and Burp Suite.
* Scripting: Learn scripting languages like Python or Bash, which are valuable for automating tasks and
developing custom tools.
5. Obtain Certifications:
* Start with foundational certifications like CompTIA Security+ to build a strong knowledge base.
* Pursue advanced certifications based on your chosen specialization, such as CISSP, CEH, OSCP, or CCSP.
6. Stay Updated:
* Follow industry news, blogs, and podcasts to stay informed about the latest trends, threats, and
technologies
in cyber security
What to Learn in Cyber Security
1. Networking and Protocols:
* Learn about IP addressing, routing, subnetting, VLANs, and network protocols like TCP/IP, DNS, and HTTP/S.
* Understand how to secure network devices, design secure network architectures, and monitor network traffic
for
anomalies.
2. Operating Systems and Virtualization:
* Gain proficiency in both Linux and Windows environments.
* Learn how to secure operating systems, manage permissions, and configure firewalls.
3. Cryptography:
* Study the principles of cryptography, including symmetric and asymmetric encryption, hashing, digital
signatures, and certificates.
* Understand how to implement encryption and key management in real-world scenarios.
4. Security Tools and Technologies:
* Familiarize yourself with essential security tools for vulnerability assessment, penetration testing,
network
monitoring, and incident response.
* Learn how to use tools like Wireshark, Nmap, Metasploit, and SIEM (Security Information and Event
Management)
systems.
5. Threat Intelligence and Incident Response:
* Study threat intelligence, including how to gather, analyze, and apply it to defend against cyber threats.
* Learn about the incident response lifecycle, including how to prepare for, detect, and respond to security
incidents.
6. Compliance and Governance:
* Understand the importance of compliance with industry regulations and standards (e.g., GDPR, HIPAA,
PCI-DSS).
* Learn about risk management, security policies, and governance frameworks.
7. Penetration Testing and Vulnerability Assessment:
* Study methodologies for identifying, exploiting, and remediating vulnerabilities in systems and
applications.
* Practice penetration testing techniques, including network, web application, and wireless security
testing.
Conclusion
By following this comprehensive guide, you can embark on a successful journey into the world of cyber security, equipping yourself with the knowledge and skills needed to protect critical digital assets and combat cyber threats.